101 | Add to Reading ListSource URL: www.ichnet.orgLanguage: English - Date: 2011-09-13 11:23:10
|
|---|
102 | Add to Reading ListSource URL: zoo.cs.yale.eduLanguage: English - Date: 2006-05-18 18:32:58
|
|---|
103 | Add to Reading ListSource URL: www.raytheon.comLanguage: English - Date: 2016-06-13 10:31:11
|
|---|
104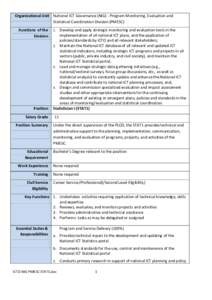 | Add to Reading ListSource URL: dict.gov.phLanguage: English - Date: 2014-12-01 02:05:56
|
|---|
105 | Add to Reading ListSource URL: www.xdtm.orgLanguage: English - Date: 2016-06-28 14:48:03
|
|---|
106 | Add to Reading ListSource URL: www.lto.orgLanguage: English - Date: 2014-09-08 23:24:42
|
|---|
107 | Add to Reading ListSource URL: junior-fellows.gi.deLanguage: English - Date: 2016-03-23 12:56:37
|
|---|
108 | Add to Reading ListSource URL: cs-www.cs.yale.eduLanguage: English - Date: 2004-05-07 13:54:31
|
|---|
109 | Add to Reading ListSource URL: www.irms.org.ukLanguage: English - Date: 2016-02-01 11:07:24
|
|---|
110 | Add to Reading ListSource URL: stakeholder.affinitywater.co.ukLanguage: English - Date: 2015-07-27 10:00:31
|
|---|